Zero-Trust Compliance ensures enterprise security, regulatory adherence, and operational resilience. Explore practical strategies, governance frameworks, and emerging technologies for a future-ready security posture.

-
Introduction to Zero-Trust Compliance
-
Core Principles of Zero-Trust Compliance
-
2.1 Verify Every User and Device
-
2.2 Least Privilege Access
-
2.3 Continuous Monitoring and Analytics
-
-
Strategic Benefits of Zero-Trust Compliance
-
3.1 Regulatory Adherence
-
3.2 Risk Mitigation
-
3.3 Operational Resilience
-
-
Practical Implementation Strategies
-
4.1 Identity and Access Management (IAM)
-
4.2 Micro-Segmentation and Network Controls
-
4.3 Security Automation and Orchestration
-
4.4 Cloud-Native and Hybrid Integration
-
-
Governance Frameworks and Policy Considerations
-
Emerging Technologies Enabling Zero-Trust Compliance
-
6.1 AI-Driven Threat Detection
-
6.2 Behavioral Analytics
-
6.3 Secure Access Service Edge (SASE)
-
-
Challenges and Best Practices
-
7.1 Common Pitfalls
-
7.2 Steps to Ensure Organizational Buy-In
-
-
Real-World Examples and Case Studies
-
Future Outlook: Zero-Trust Compliance as a Business Enabler
-
Conclusion
-
Introduction to Zero-Trust Compliance
Zero-Trust Compliance has become essential for enterprises facing evolving cyber threats, regulatory demands, and complex IT environments. Unlike traditional security models that implicitly trust internal networks, Zero-Trust assumes no user or device is inherently trustworthy. Every access request must be verified, monitored, and authorized, providing a robust foundation for security and compliance.
Organizations adopting Zero-Trust frameworks ensure continuous verification, granular access controls, and audit-ready systems, reducing risk and maintaining operational resilience.
2. Core Principles of Zero-Trust Compliance
2.1 Verify Every User and Device
Identity verification is central to Zero-Trust Compliance. Implement multi-factor authentication (MFA), device attestation, and identity federation to ensure only authorized users and devices gain access. Identity-centric security supports regulatory requirements and prevents unauthorized access.
2.2 Least Privilege Access
Granting minimum necessary permissions reduces the attack surface. Least privilege access ensures that compromised accounts cannot propagate attacks across systems, safeguarding sensitive data.
2.3 Continuous Monitoring and Analytics
Continuous monitoring enables real-time detection of anomalies, insider threats, and unauthorized activity. AI and behavioral analytics can augment monitoring, providing actionable insights and automated responses.
Zero-Trust Compliance: The Strategic Imperative for Modern Enterprise Security
In an era where cyber threats evolve at an unprecedented pace, traditional perimeter-based security models are no longer sufficient. Enterprises face increasingly sophisticated attacks, regulatory pressures, and a rapidly expanding attack surface due to cloud adoption, remote work, and IoT proliferation. Against this backdrop, Zero-Trust Compliance has emerged as the cornerstone of modern cybersecurity strategy.
Unlike conventional security paradigms that implicitly trust internal users or devices, a Zero-Trust framework operates on the principle of “never trust, always verify.” It enforces strict identity verification, continuous monitoring, and granular access controls across all networks, applications, and devices. Implementing Zero-Trust Compliance is not merely a technical necessity; it is a strategic business enabler, ensuring regulatory adherence, operational resilience, and long-term enterprise scalability.
-
-
Accelerate digital transformation initiatives
-
Secure remote work and hybrid operations
-
Enhance customer trust through robust security assurances
-
-
Financial Sector: A global bank implemented Zero-Trust Compliance, segmenting critical applications and enforcing MFA across all users. Result: Reduced breach incidents by 60% while ensuring GDPR compliance.
-
-
Engage executives and stakeholders early
-
Provide training and awareness programs
-
Gradually implement Zero-Trust policies to avoid operational disruptionHealthcare: A hospital network adopted micro-segmentation and continuous monitoring for its EHR systems. Result: Improved HIPAA compliance and minimized insider threat risks.Enable scalable, flexible, and resilient enterprise architectures
Introduction to Zero-Trust Compliance
Zero-Trust Compliance represents a paradigm shift in cybersecurity. Traditional models rely on firewalls, VPNs, and trusted internal networks to secure systems, assuming that internal users are inherently safe. However, the modern enterprise environment is far more complex: employees access applications from remote locations, contractors and third-party vendors require temporary access, and sensitive data resides across cloud platforms and SaaS applications.
Zero-Trust removes assumptions of implicit trust. Every access request is authenticated, authorized, and continuously validated, regardless of whether it originates inside or outside the network. Compliance in this context means aligning Zero-Trust principles with industry standards, legal regulations, and security best practices, ensuring that the organization is audit-ready and resilient against evolving threats.
2. Core Principles of a Zero-Trust Framework
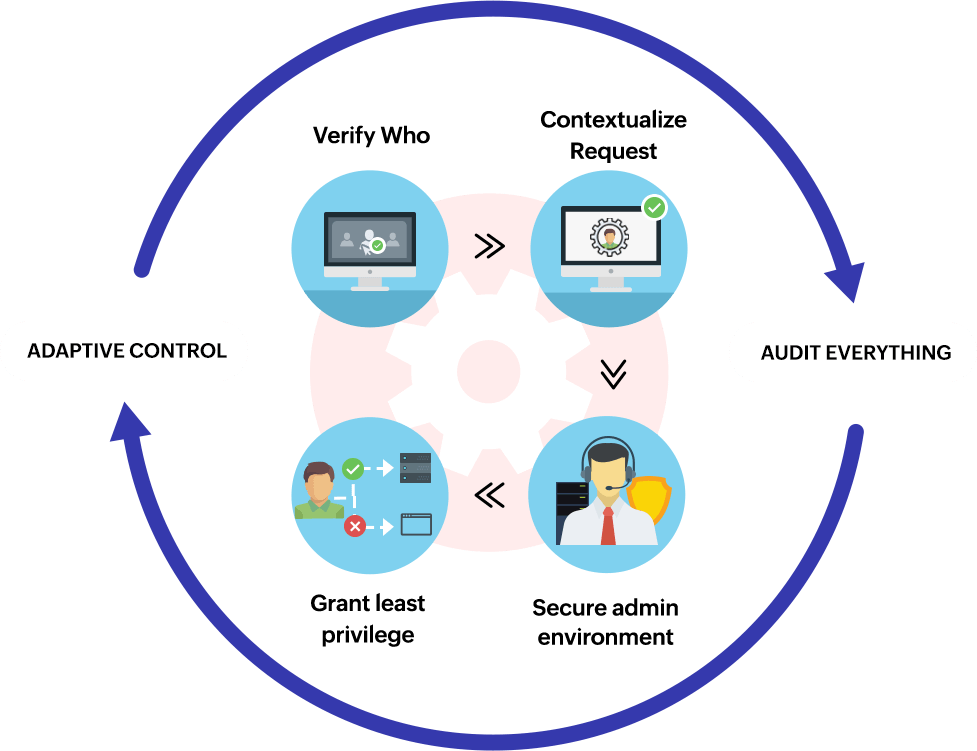
2.1 Verify Every User and Device
Identity is the new perimeter. Zero-Trust frameworks require strong authentication mechanisms, including multi-factor authentication (MFA), device attestation, and identity federation. This ensures that only verified users and devices can access critical systems. Identity-based policies form the foundation of regulatory compliance by controlling who can access sensitive data and under what conditions.
2.2 Least Privilege Access
Zero-Trust enforces least privilege principles, granting users and devices only the access necessary to perform their tasks. By limiting permissions, organizations reduce the risk of lateral movement in case of compromise. This is particularly important for high-value assets such as customer databases, intellectual property, and financial systems.
2.3 Continuous Monitoring and Analytics
Zero-Trust relies on continuous monitoring of network traffic, user behavior, and access patterns. Real-time analytics detect anomalies, unauthorized access attempts, and potential insider threats. Automated alerts and incident response workflows ensure rapid mitigation, minimizing damage and maintaining regulatory compliance.
3. Strategic Benefits of Zero-Trust Compliance
3.1 Regulatory Adherence
Industries such as finance, healthcare, and government face stringent regulatory requirements like GDPR, HIPAA, PCI DSS, and SOX. Zero-Trust frameworks help organizations maintain compliance-ready environments by enforcing access controls, detailed auditing, and secure handling of sensitive information.
3.2 Risk Mitigation
Zero-Trust reduces exposure to cyber threats by eliminating implicit trust, segmenting networks, and continuously verifying access. Organizations can prevent common attack vectors such as phishing, ransomware, and credential theft, significantly lowering the risk profile.
3.3 Operational Resilience
By implementing granular controls and continuous monitoring, Zero-Trust ensures that critical business processes remain protected during cyber incidents. Operational continuity is maintained even under attack, minimizing downtime, financial losses, and reputational damage.
4. Practical Implementation Strategies
4.1 Identity and Access Management (IAM)
IAM systems are central to Zero-Trust Compliance. Organizations must implement role-based access control (RBAC), adaptive authentication, and single sign-on (SSO) to ensure secure and efficient user management. Continuous audits and access reviews maintain compliance and reduce the risk of over-privileged accounts.
4.2 Micro-Segmentation and Network Controls
Segmenting networks into isolated zones prevents attackers from moving laterally. Each segment has its own security policies, access controls, and monitoring systems. This micro-segmentation is critical for protecting sensitive assets and ensuring compliance with regulatory standards.
4.3 Security Automation and Orchestration
Automated workflows streamline threat detection, incident response, and policy enforcement. AI-driven automation can correlate logs, detect anomalies, and trigger real-time remediation, reducing human error and accelerating response times.
4.4 Cloud-Native and Hybrid Integration
Zero-Trust frameworks must accommodate hybrid environments, including on-premises systems, public clouds, and SaaS applications. Secure access service edge (SASE) models and cloud-native security solutions enable unified policy enforcement across distributed infrastructures.
5. Governance Frameworks and Policy Considerations
Effective Zero-Trust Compliance requires clear governance policies. Organizations must define:
-
Roles and responsibilities for IT and security teams
-
Policy lifecycle management
-
Continuous monitoring and auditing processes
-
Incident response and escalation protocols
Strong governance ensures alignment between technical controls and business objectives while supporting regulatory and audit requirements.
6. Emerging Technologies Enabling Zero-Trust
6.1 AI-Driven Threat Detection
Artificial intelligence identifies patterns, predicts anomalies, and enhances threat detection in real-time, making Zero-Trust frameworks smarter and more responsive.
6.2 Behavioral Analytics
Monitoring user behavior and device activity allows organizations to detect deviations from normal patterns, reducing insider threats and credential misuse.
6.3 Secure Access Service Edge (SASE)
SASE combines network security functions with WAN capabilities, enabling secure cloud access and consistent Zero-Trust enforcement across distributed environments.
7. Challenges and Best Practices
7.1 Common Pitfalls
-
Underestimating cultural change required for Zero-Trust adoption
-
Overly complex policies that hinder productivity
-
Neglecting continuous monitoring and auditing
7.2 Steps to Ensure Organizational Buy-In
-
8. Real-World Examples and Case Studies
-
-
Financial Sector: A global bank implemented Zero-Trust Compliance, segmenting critical applications and enforcing MFA across all users. Result: Reduced breach incidents by 60% while ensuring GDPR compliance.
-
Healthcare: A hospital network adopted micro-segmentation and continuous monitoring for its EHR systems. Result: Improved HIPAA compliance and minimized insider threat risks.
9. Future Outlook: Zero-Trust as a Business Enabler
Zero-Trust is evolving beyond security—it is a strategic differentiator. Organizations that adopt this framework c
-
10. Conclusion
Zero-Trust Compliance is no longer optional. By eliminating implicit trust, enforcing rigorous verification, and continuously monitoring access, enterprises can achieve a resilient, scalable, and compliant security posture. Beyond protection, Zero-Trust acts as a strategic business enabler, supporting innovation, regulatory adherence, and operational excellence in 2025 and beyond.
At HexaMileSoft, we help organizations implement Zero-Trust frameworks that combine cutting-edge technology, governance, and best practices to deliver secure, compliant, and future-ready enterprise solutions.
-